I probably should have done this post first, because what you do here can be used in the previous hack using these rainbow files. Using Ophcrack, you can crack account password of almost all the Windows operating systems currently used in industry (i have not tested this on Windows8, but i assume it would work as long as they don't use "draw your password" feature) and since OphCrack is the fastest password cracking tool, it wont take more than 30 minutes to crack a password. So let's begin:
What Do You Need ?
BackTrack 5 Live DVD/USB.
Rainbow Files (i'll tell you what it is.)
Physical Access to victim PC.
So What-The-Hell is Rainbow Files ?
First thing that pops in mind when reading rainbow files is the collection of rainbows and unicorns flying(sarcasm), but no, rainbow files/tables are basically huge sets of precomputed tables filled with hash values that are pre-matched to possible plaintext passwords. The rainbow tables essentially allow hackers to reverse the hashing function to determine what the plaintext password might be. It's possible for two different passwords to result in the same hash so it's not important to find out what the original password was, just as long as it has the same hash. The plaintext password may not even be the same password that was created by the user, but as long as the hash is matched, then it doesn't matter what the original password was.
So What Do I Need To Do ?
You need to download the rainbow tables matching to the OS version of your victim PC. Get them Here.You can download the smaller files because they will work,unless your victim uses 28+ key long password.
NOTE: the vista files will work for Windows 7 and Windows 8 too.
Everything is Downloaded and ready, now put the downloaded rainbow tables on a flash drive.
Let's begin;
Step 1:
Boot the victim PC with BackTrack Live DVD. remember to start the GUI (startx)
Step 2:
Now navigate to the directory where windows password files are stored.
usually: WINDOWS/system32/config/
Step 3:
Locate the Files "SAM" and "System", and copy them to a new folder on the desktop of Backtrack
Step 4:
Run the OphCrack tool in backtrack by : start->Backtrack->Privilege Escalation->Password Attack->Offline Attacks->Ophcrack GUI.
Step 5:
Go to "Load" and select "Encrypted SAM" in ophcrack tool. Now it will ask you to select directory that contains SAM folder. Select the directory where you saved the SAM file (new folder on desktop).
Step 6:
Target the Administrator account, remove other account off the list (if any).
Step 7:
Plug in the pen-drive/flash drive, extract the rainbow tables to desktop.
Step 8:
Click on the "Table" button in ophcrack tool. Now it will ask you to select the table. Select the files as required.Click OK after that.
Step 9:
Now hit the "Crack" button, and wait a few minutes, you should have the key. reboot the windows machine into windows and test.
nonsensical common
Tuesday, March 12, 2013
Wednesday, February 27, 2013
LAN Hacking
I'm posting this hack first because its easy to do, and it will get your feet wet as to what can be done with the right tools and enough patience. the goal for this hack is to show you what kind of damage an attacker who gains access to your LAN environment can do if left to his/her own devices. the major tool i will use is Metasploit, bu ti will simplify this for you because this is your first time hacking into anything, so i'm also using ARMITAGE. Armitage is an GUI Platform for Metaspoilt and in technical terms,it is a script-able red team collaboration tool for Metasploit that visualizes targets, recommends exploits, and exposes the advanced post-exploitation features in the framework.It saves time and is very powerful in commencing Metaspoilt attacks.
So Now about our attack:
What we need:
Latest Metasploit framework.
Java
Preferably Internet on LAN
Brains and patience.
Now lets us start our hack:
Step 1: Open armitage on Backtrack 5 by going to : Backtrack > Exploitation Tools > Network Exploitation Tools > Metasploit Framework > armitage.
Step 2: Connect Armitage:
Click on the connect button.
Step 3: Connecting Armitage :
Now use the patience part, and stretch your legs, it takes some time to connect.
Step 4: Armitage Window :
It has 3 Panels:
Target Panel
Module Panel
Tabs Panel
Step 5: Finding the alive host on the network :
Now you will search for Host on you network, by going to hosts -> Nmap Scan -> Quick Scan (OS detect). This will perform a quick scan to detect the host and their operating systems and vulnerabilities.
Step 6: Inputting The Scan Range :
Now You have to insert scan range,that is you LAN ip range, most preferably it would start with 192.168.0.- or 10.0.0.-.
NOTE : the ( - ) resembles the computers on LAN.
Start the scan.
Step 7: Scan complete: After the scan has completed, if their are any other PC's on your network on, then they would be visible in the Target Pane (the big black box on the upper right).
Step 8: Finding Attacks :
Now the fun parts starts. Click on "Attacks" tab in your toolbar and select 'find attacks' (Not hail mary, you might not be ready for that). Start the scan and wait till it completes.
Step 9: Set the vulnerability :
Right click on the 'host' icon (windows pc) -> Select attacks -> smb -> ms08_067_netapi vulnerability.
Now a window should pop, click on the check-box that says "Use a reverse connection", start attack
Step 10: The final result :
So did the host icon turn red? That means YOU PASSED.
So you did the hacking part right, now let us mess with the client.
Hack 1: Opening Command Prompt:
Right click on the host -> Meterpreter1 ->Interact -> Command Shell
Now you are in their command prompt. You can now change, rename, delete, create files on their pc now. Search Google for some powerful windows commands.
Hack 2: Start an KEYLOGGER:
Click on the Meterpreter2 -> Explore -> Log Keystrokes.
Now you will receive what the victim is typing.
Hack 3: Take a Screen Shot:
Click on the Meterpreter2 -> Explore ->Screenshot.
Now you can see what is on their Facebook wall or Google mail accounts.
Hack 4: Browse Files:
Right click -> Meterpreter2 -> Explore > Browse Files .
Now you can interact with all the files on victim PC via a GUI.
Hack 5: Get in His Webcam:
Right click -> Meterpreter2 ->Explore -> Webcam shot
If they have a webcam installed, this will stream to you what the camera sees.
This will get you started. Please try and do your own discovery, and research as much as possible. The habit of self discovery can fetch you far more knowledge than someone holding your hand and showing you the say.
Happy Hacking!
So Now about our attack:
What we need:
Latest Metasploit framework.
Java
Preferably Internet on LAN
Brains and patience.
Now lets us start our hack:
Step 1: Open armitage on Backtrack 5 by going to : Backtrack > Exploitation Tools > Network Exploitation Tools > Metasploit Framework > armitage.
Step 2: Connect Armitage:
Click on the connect button.
Step 3: Connecting Armitage :
Now use the patience part, and stretch your legs, it takes some time to connect.
Step 4: Armitage Window :
It has 3 Panels:
Target Panel
Module Panel
Tabs Panel
Step 5: Finding the alive host on the network :
Now you will search for Host on you network, by going to hosts -> Nmap Scan -> Quick Scan (OS detect). This will perform a quick scan to detect the host and their operating systems and vulnerabilities.
Step 6: Inputting The Scan Range :
Now You have to insert scan range,that is you LAN ip range, most preferably it would start with 192.168.0.- or 10.0.0.-.
NOTE : the ( - ) resembles the computers on LAN.
Start the scan.
Step 7: Scan complete: After the scan has completed, if their are any other PC's on your network on, then they would be visible in the Target Pane (the big black box on the upper right).
Step 8: Finding Attacks :
Now the fun parts starts. Click on "Attacks" tab in your toolbar and select 'find attacks' (Not hail mary, you might not be ready for that). Start the scan and wait till it completes.
Step 9: Set the vulnerability :
Right click on the 'host' icon (windows pc) -> Select attacks -> smb -> ms08_067_netapi vulnerability.
Now a window should pop, click on the check-box that says "Use a reverse connection", start attack
Step 10: The final result :
So did the host icon turn red? That means YOU PASSED.
So you did the hacking part right, now let us mess with the client.
Hack 1: Opening Command Prompt:
Right click on the host -> Meterpreter1 ->Interact -> Command Shell
Now you are in their command prompt. You can now change, rename, delete, create files on their pc now. Search Google for some powerful windows commands.
Hack 2: Start an KEYLOGGER:
Click on the Meterpreter2 -> Explore -> Log Keystrokes.
Now you will receive what the victim is typing.
Hack 3: Take a Screen Shot:
Click on the Meterpreter2 -> Explore ->Screenshot.
Now you can see what is on their Facebook wall or Google mail accounts.
Hack 4: Browse Files:
Right click -> Meterpreter2 -> Explore > Browse Files .
Now you can interact with all the files on victim PC via a GUI.
Hack 5: Get in His Webcam:
Right click -> Meterpreter2 ->Explore -> Webcam shot
If they have a webcam installed, this will stream to you what the camera sees.
This will get you started. Please try and do your own discovery, and research as much as possible. The habit of self discovery can fetch you far more knowledge than someone holding your hand and showing you the say.
Happy Hacking!
Thursday, February 21, 2013
Top 9 penetration testing operating systems
Below is the list of Top 9 Operating Systems focused on Penetration and Hacking,The Operating Systems are judged on these Criteria : Number Of Package's, Availability of tutorials,how often new editions come out, popularity and user experience. I have personally used each of these tools, and i must say they do live up to their name and reputation.
One Operating System of note:
Damn Vulnerable Linux.
Well this is new, Damn Vulnerable Linux (DVL) is everything a good Linux distribution isn't; Its developers have spent hours stuffing it with broken, ill-configured, outdated, and exploitable software that makes it vulnerable to attacks. Based on Slackware, DVL isn't built to run on your desktop – it’s a learning tool for security students. So put it on your old PC and start your hacking carrier.
NOTE: This is not a distro full of security tools and how-to-hack apps. This is one of the best tools to use as a target to test your skills against. The people who developed this have sense discontinued the project, but you can still find ISO's and virtual images of this product for your own use.
NOTE: ITT Technical Institute students are given a copy of this on a virtual machine with their server farm structure for ISS classes. It is labeled as one of their Linux VM's
With that, here it is:
Number 9 : Samurai Web Testing Framework (WTF).
The Samurai Web Testing Framework is a live Linux environment that has been pre-configured to function as a web pen-testing environment. The CD contains the best of the open source and free tools that focus on testing and attacking websites. Developed by Kevin Johnson [security analyst] and Justin Searle [IT Security Architect for JetBlue Airways] specially for hacking web based application and websites. Bad thing it is only available as Live DVD, and its one of more difficult distro's to install. Interested ? then check out their page Here.
Number 8 : Back Box Linux.
BackBox is a Linux distribution based on Ubuntu. It has been developed to perform penetration tests and security assessments. Designed to be fast, easy to use and provide a minimal yet complete desktop environment, its own software repositories, are always being updated to the latest stable version of the most used and best known ethical hacking tools. Check it out Here.
Number 7 : Gnacktrack :
Ahh, gnackTrack is no-doubt the best looking Pentesting operating system ever,and this is the best for beginner hackers,it has a good software library,GnackTrack is a Live (and installable) Linux distribution based on Ubuntu.The latest version "GnackTrackR6" is gaining a lot of popularity and you should try it out if you are interested.Official Site Here.
Number 6 : Network Security Toolkit (NST).
The Network Security Toolkit (NST) is Based of Fedora (not debian ) and The main intent of developing this toolkit was to provide the network security administrator with a comprehensive set of Open Source Network Security Tools.This Distro has a whole new level of Graphical Interface and damm it looks good.Get this beautiful yet dangerous OS Here.
Number 5 : Live Hacking Operating System.

Live Hacking DVD is a Linux distribution packed with tools and utilities for ethical hacking, penetration testing and countermeasure verification. Based on Ubuntu this distribution comes in two forms. A full Linux desktop including a graphical user interface (GNOME) and tools and utilities..Another in live DVD form.Plus Point : This distro has a huge guide on hacking on its official site.Get this Distro Here
Number 4 :DEFT Digital Evidence & Forensic Toolkit.
.jpg)
DEFT 7 is based on the new Kernel 3 (Linux side) and the DART (Digital Advanced Response Toolkit) with the best freeware Windows Computer Forensic tools. It’s a new concept of Computer Forensic system that use LXDE as desktop environment.It is a very professional and stable system that includes an excellent hardware detection and the best free and open source applications dedicated to Incident Response, Cyber Intelligence and Computer Forensics.Get this Swiss Army Knife of the PC world Here
Number 3 : BlackBuntu Linux.
Blackbuntu is distribution for penetration testing which was specially designed for security training students and practitioners of information security. It's currently being built using the xubuntu 12.04.This edition has a large software library and nearly 100000's tutorials flying on YouTube and other sites. Blackbuntu runs on almost any PC,new or old,because of its less requirements.The Main developer,Krit Kadnok says "It's created in our own time as a hobby."Get Blackbuntu Here.
Number 2 : BugTraq Operating System.
 Bugtraq system offers the most comprehensive distribution, optimal, and stable with automated services manager in real time. Bugtraq is available with XFCE, Gnome and KDE based on Ubuntu, Debian and OpenSuse. The systems are available in 11 different languages. Bugtraq has the widest range of tools and a whole lot of tutorials on the net,besides that,This distro has a sick interface.Get this Here.
Bugtraq system offers the most comprehensive distribution, optimal, and stable with automated services manager in real time. Bugtraq is available with XFCE, Gnome and KDE based on Ubuntu, Debian and OpenSuse. The systems are available in 11 different languages. Bugtraq has the widest range of tools and a whole lot of tutorials on the net,besides that,This distro has a sick interface.Get this Here.
Number 1 : BackTrack Operating System.
.jpg)
BackTrack is an Operating system which is especially made for Hackers,ethical Hackers,Penetration testers etc.This operating system includes all the security assessments and features till date.This distro got it all,Slick Interface,Powerful yet latest tools,high compatibly large software library,tons of tutorial.you name it.This is used by FBI,NSA and most of the hackers.So why don't you try it ? Get Version 5r3 from Here.
One Operating System of note:
Damn Vulnerable Linux.

Well this is new, Damn Vulnerable Linux (DVL) is everything a good Linux distribution isn't; Its developers have spent hours stuffing it with broken, ill-configured, outdated, and exploitable software that makes it vulnerable to attacks. Based on Slackware, DVL isn't built to run on your desktop – it’s a learning tool for security students. So put it on your old PC and start your hacking carrier.
NOTE: This is not a distro full of security tools and how-to-hack apps. This is one of the best tools to use as a target to test your skills against. The people who developed this have sense discontinued the project, but you can still find ISO's and virtual images of this product for your own use.
NOTE: ITT Technical Institute students are given a copy of this on a virtual machine with their server farm structure for ISS classes. It is labeled as one of their Linux VM's
With that, here it is:
Number 9 : Samurai Web Testing Framework (WTF).

The Samurai Web Testing Framework is a live Linux environment that has been pre-configured to function as a web pen-testing environment. The CD contains the best of the open source and free tools that focus on testing and attacking websites. Developed by Kevin Johnson [security analyst] and Justin Searle [IT Security Architect for JetBlue Airways] specially for hacking web based application and websites. Bad thing it is only available as Live DVD, and its one of more difficult distro's to install. Interested ? then check out their page Here.
Number 8 : Back Box Linux.

BackBox is a Linux distribution based on Ubuntu. It has been developed to perform penetration tests and security assessments. Designed to be fast, easy to use and provide a minimal yet complete desktop environment, its own software repositories, are always being updated to the latest stable version of the most used and best known ethical hacking tools. Check it out Here.
Number 7 : Gnacktrack :

Ahh, gnackTrack is no-doubt the best looking Pentesting operating system ever,and this is the best for beginner hackers,it has a good software library,GnackTrack is a Live (and installable) Linux distribution based on Ubuntu.The latest version "GnackTrackR6" is gaining a lot of popularity and you should try it out if you are interested.Official Site Here.
Number 6 : Network Security Toolkit (NST).

The Network Security Toolkit (NST) is Based of Fedora (not debian ) and The main intent of developing this toolkit was to provide the network security administrator with a comprehensive set of Open Source Network Security Tools.This Distro has a whole new level of Graphical Interface and damm it looks good.Get this beautiful yet dangerous OS Here.
Number 5 : Live Hacking Operating System.

Live Hacking DVD is a Linux distribution packed with tools and utilities for ethical hacking, penetration testing and countermeasure verification. Based on Ubuntu this distribution comes in two forms. A full Linux desktop including a graphical user interface (GNOME) and tools and utilities..Another in live DVD form.Plus Point : This distro has a huge guide on hacking on its official site.Get this Distro Here
Number 4 :DEFT Digital Evidence & Forensic Toolkit.
.jpg)
DEFT 7 is based on the new Kernel 3 (Linux side) and the DART (Digital Advanced Response Toolkit) with the best freeware Windows Computer Forensic tools. It’s a new concept of Computer Forensic system that use LXDE as desktop environment.It is a very professional and stable system that includes an excellent hardware detection and the best free and open source applications dedicated to Incident Response, Cyber Intelligence and Computer Forensics.Get this Swiss Army Knife of the PC world Here
Number 3 : BlackBuntu Linux.

Blackbuntu is distribution for penetration testing which was specially designed for security training students and practitioners of information security. It's currently being built using the xubuntu 12.04.This edition has a large software library and nearly 100000's tutorials flying on YouTube and other sites. Blackbuntu runs on almost any PC,new or old,because of its less requirements.The Main developer,Krit Kadnok says "It's created in our own time as a hobby."Get Blackbuntu Here.
Number 2 : BugTraq Operating System.
 Bugtraq system offers the most comprehensive distribution, optimal, and stable with automated services manager in real time. Bugtraq is available with XFCE, Gnome and KDE based on Ubuntu, Debian and OpenSuse. The systems are available in 11 different languages. Bugtraq has the widest range of tools and a whole lot of tutorials on the net,besides that,This distro has a sick interface.Get this Here.
Bugtraq system offers the most comprehensive distribution, optimal, and stable with automated services manager in real time. Bugtraq is available with XFCE, Gnome and KDE based on Ubuntu, Debian and OpenSuse. The systems are available in 11 different languages. Bugtraq has the widest range of tools and a whole lot of tutorials on the net,besides that,This distro has a sick interface.Get this Here.Number 1 : BackTrack Operating System.
.jpg)
BackTrack is an Operating system which is especially made for Hackers,ethical Hackers,Penetration testers etc.This operating system includes all the security assessments and features till date.This distro got it all,Slick Interface,Powerful yet latest tools,high compatibly large software library,tons of tutorial.you name it.This is used by FBI,NSA and most of the hackers.So why don't you try it ? Get Version 5r3 from Here.
Man-in-the-middle attacks using Ettercap
Introduction To Man-In-The-Middle Attacks -
Man in the middle attacks is known as eavesdropping in the computer world. In these attacks, the attackers makes a fake bridge connections with the victims and relays message so they think that the connection is working the way it is supposed to work. With this connection, the attacker can see all the same traffic that the victim sees. Basic man-in-the-middle attacks are easily stopped by employing a VPN; so you can see the importance of using a VPN when using public internet.
Introduction To ETTERCAP -
Ettercap,short for Ethernet Capture,Is an open source app that creates an fake connection to your victim and the router,captures and send's data to its destination.It features sniffing of live connections, content filtering on the fly and many other interesting tricks. It supports active and passive dissection of many protocols and includes many features for network and host analysis.
Installing ETTERCAP -
For Debian (Linux) based editions -
Debian based editions (Ubuntu,backtrack,etc) can install Ettercap by using these steps -
1-Open Your Terminal.
2-Type: sudo apt-get install ettercap-gtk ettercap-common
3 -When you have installed it, type on the terminal: sudo gedit /etc/etter.conf
4 - Look for something like "iptables" and delete the #.
5 -It Should look like:
redir_command_on = "iptables -t nat -A PREROUTING -i %iface -p tcp --dport %port -j REDIRECT --to-port %rport".
-what this does is route connections from your incoming to the outgoing internet connection on your machine; this will make the victim unaware that someone is spying on their traffic.
For Windows based editions -
1-Get the installer from Here
2 -Install it by using the on-screen steps.
Setting Up ETTERCAP -
1 - Run the application.
2 - Click "Sniff -Unified Sniffing",then choose the network from the drop-down list you want to attack.
3 - Once you have chosen the interface the something like this will open:
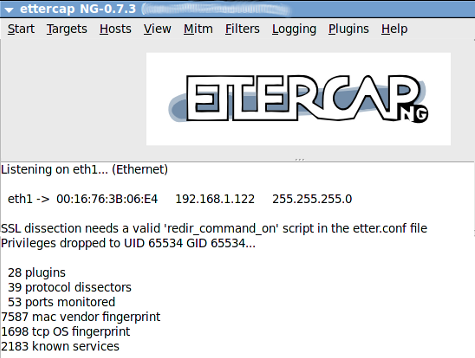
4 - Now go to - “Hosts->Scan for Host",now it will scan the network for other computers.
5 - When completed,click on "Hosts-> Host List",it will show up the available computers.
6 - Now select the computer you want to attack (example 192.168.0.5) as TARGET 1,And the ip of router (example 192.168.0.1) as TARGET 2.
7 - Now go to "MITM -> Arp Poisoning,and select the “Sniff Remote Connection” and click “ok”.
8 - Click "Start" and choose "Start Sniffing".
How Could the Attacker use this data -
The captured data can be easily used for sniffing password for Google Facebook,yahoo etc and they can also use it as a monitoring device,and see what kind of porn you like :P
NOTE : ETTERCAP can cause instability of network and the windows version is not too much stable, Restart the router in order to regain stability.
Thursday, January 17, 2013
resetting passwords in Windows8/7
Here I will try to make an easy to follow tutorial that will be usefull for novice users as well as professionals when they get stuck behind the logon screen of a Windows 8 because they lost or forgotten their password. So here's how to do it in 10 minutes or less :

24- confirm the new password when prompted and hit Enter key when done:

25- Type exit and hit the Enter key to close the command window.
26- Logon now to the locked account with the new password you just created.

27- After successfully unlocking your account and resetting the account password now you need to roll back the changes youmade to Utilman.exe and cmd.exe, so go ahead and boot your pc with the System Recovery CD or USB you made earlier in thistutorial and repeat steps in # 6 so you open the command prompt window
28- Type: c: and hit Enter key(your Windows drive maybe different so change it accordingly to the drive letter you have)
29- Type: cd windows (watch for spaces) and hit Enter key [see picture below]
30- Type: cd system32 (watch for spaces) and hit Enter key [see picture below]
31- Type: del Utilman.exe (watch for spaces) and hit Enter key [see picture below]
32- Type: ren Utilman.exe.original Utilman.exe (watch for spaces) and hit Enter key [see picture below]
33- Type: ren cmd.exe.original cmd.exe (watch for spaces) and hit Enter key [see picture below]
34- Type: shutdown -r -t 00 (watch for spaces) and hit Enter key to reboot your pc [see picture below]

35- Now when the pc reboots and reaches the logon screen, check to see if the Utilman is fixed and returned back to place by clicking on its icon on the bottom left side of the screen, if the Ease of Access list pops up then you succeeded in your work.
PS: some of you might have a Windows 8 Installation DVD, he can use it also in this process, boot with this Windows DVD and when you reach the first screen where you have to click next - stop there and hit SHIFT key + F 10 , the command prompt window will pop up and you can use it as we did in steps 7 onward to the end.
1- You need a Windows 8 PC to make a System Recovery Disk .
2- You need a CD Burner + Blanck CD.
3- If you have a tablet or a netbook and you don't have a CD burner then You need a 512 MB USB thumb drive to make a System Recovery USB instead.
4- To make a system recovery CD, Go to control panel and navigate to Windows 7 File Recovery, click on that icon, and from the next screen choose from the top left ( Create a System Recovery Disk ) and follow the on-screen instructions to make that CD.
5- To make a System Recovery USB thumb drive go to control panel and navigate to ( Recovery ), click on that icon and from the next screen choose ( Create a recovery drive ) and follow the instructions to make a bootable System Recovery USB.
6- When you are ready, boot the locked PC that needs to be unlocked with that CD or USB you just made, and follow the pictures below :


7- The command prompt screen will open, type : diskpart and hit Enter key

2- You need a CD Burner + Blanck CD.
3- If you have a tablet or a netbook and you don't have a CD burner then You need a 512 MB USB thumb drive to make a System Recovery USB instead.
4- To make a system recovery CD, Go to control panel and navigate to Windows 7 File Recovery, click on that icon, and from the next screen choose from the top left ( Create a System Recovery Disk ) and follow the on-screen instructions to make that CD.
5- To make a System Recovery USB thumb drive go to control panel and navigate to ( Recovery ), click on that icon and from the next screen choose ( Create a recovery drive ) and follow the instructions to make a bootable System Recovery USB.
6- When you are ready, boot the locked PC that needs to be unlocked with that CD or USB you just made, and follow the pictures below :


7- The command prompt screen will open, type : diskpart and hit Enter key

8- Type : list vol and hit Enter key (watch for spaces)

9- locate your Windows partition letter ( in our case here the letter will be C drive)
10- Type : Exit and hit Enter key.

11- Type: c: and hit Enter key (your Windows drive maybe different so change it accordingly to the drive letter you have)

12- Type: cd windows (watch for spaces ) and hit Enter key

13- Type: cd system32 (watch for spaces) and hit Enter key

14- Type: copy cmd.exe cmd.exe.original (watch for spaces) and hit Enter key.

15- Type: copy Utilman.exe Utilman.exe.original (watch for spaces) and hit Enter key.

16- Type: del Utilman.exe (watch for spaces) and hit Enter key.

17- Type: ren cmd.exe Utilman.exe (watch for spaces) and hit Enter key.

18- Type: Shutdown -r -t 00 (watch for spaces) and hit Enter key, the PC will restart.

19 – When you reach the Logon screen click on the Ease of Access Center icon on the left bottom side of the screen.
20 – The command prompt window will open
21- Type: net user (watch for spaces) and hit Enter key.

22- Type: net user <username> * ( replace <username> with the name you find in your pc) and hit Enter key
23- now type the new password you want and hit Enter key( when you type the cursor will not move and you will not see what you type, so be carefull what you type, because you are typing blindly the new password)

9- locate your Windows partition letter ( in our case here the letter will be C drive)
10- Type : Exit and hit Enter key.

11- Type: c: and hit Enter key (your Windows drive maybe different so change it accordingly to the drive letter you have)

12- Type: cd windows (watch for spaces ) and hit Enter key

13- Type: cd system32 (watch for spaces) and hit Enter key

14- Type: copy cmd.exe cmd.exe.original (watch for spaces) and hit Enter key.

15- Type: copy Utilman.exe Utilman.exe.original (watch for spaces) and hit Enter key.

16- Type: del Utilman.exe (watch for spaces) and hit Enter key.

17- Type: ren cmd.exe Utilman.exe (watch for spaces) and hit Enter key.

18- Type: Shutdown -r -t 00 (watch for spaces) and hit Enter key, the PC will restart.

19 – When you reach the Logon screen click on the Ease of Access Center icon on the left bottom side of the screen.
20 – The command prompt window will open
21- Type: net user (watch for spaces) and hit Enter key.

22- Type: net user <username> * ( replace <username> with the name you find in your pc) and hit Enter key
23- now type the new password you want and hit Enter key( when you type the cursor will not move and you will not see what you type, so be carefull what you type, because you are typing blindly the new password)

24- confirm the new password when prompted and hit Enter key when done:

25- Type exit and hit the Enter key to close the command window.
26- Logon now to the locked account with the new password you just created.

27- After successfully unlocking your account and resetting the account password now you need to roll back the changes youmade to Utilman.exe and cmd.exe, so go ahead and boot your pc with the System Recovery CD or USB you made earlier in thistutorial and repeat steps in # 6 so you open the command prompt window
28- Type: c: and hit Enter key(your Windows drive maybe different so change it accordingly to the drive letter you have)
29- Type: cd windows (watch for spaces) and hit Enter key [see picture below]
30- Type: cd system32 (watch for spaces) and hit Enter key [see picture below]
31- Type: del Utilman.exe (watch for spaces) and hit Enter key [see picture below]
32- Type: ren Utilman.exe.original Utilman.exe (watch for spaces) and hit Enter key [see picture below]
33- Type: ren cmd.exe.original cmd.exe (watch for spaces) and hit Enter key [see picture below]
34- Type: shutdown -r -t 00 (watch for spaces) and hit Enter key to reboot your pc [see picture below]

35- Now when the pc reboots and reaches the logon screen, check to see if the Utilman is fixed and returned back to place by clicking on its icon on the bottom left side of the screen, if the Ease of Access list pops up then you succeeded in your work.
PS: some of you might have a Windows 8 Installation DVD, he can use it also in this process, boot with this Windows DVD and when you reach the first screen where you have to click next - stop there and hit SHIFT key + F 10 , the command prompt window will pop up and you can use it as we did in steps 7 onward to the end.
setting up a VPN
If you want secure access to your network when away from the office, you can setup a Virtual Private Network (VPN ). You can connect via the Internet and securely access your shared files and resources. You don't have to buy an expensive VPN server if don't have a lot of users. Windows actually provides VPN server and client functionality.
In this tutorial, we'll set up the Windows 7 or Vista VPN server and connect with Windows XP, Vista, or 7. Now let's get started!
Avoiding IP conflicts
Since VPN connections link networks together, you must be careful with the subnet and IP addressing so there aren't any conflicts. On the network hosting the VPN server, you should use an uncommon default IP for the router, such as 192.168.50.1. If you have multiple offices, assign each to a different uncommon IP/subnet, such as 192.168.51.1, 192.168.52.1, and so on.

Create an incoming VPN connection in Windows
To configure the Windows VPN server, you do what is described by Microsoft as "creating an incoming connection." This will be the server or host of the VPN. Among other things, you'll specify the users you want to be able to connect. Follow these steps to create an incoming connection:
- Right-click the network icon in the system tray and select Open Network and Sharing Center.
- Click on Manage network connections (Windows Vista) or Change adapter settings (Windows 7).
- Press the Alt key to show the File Menu and click File > New Incoming connection… .
- Select who you'd like to give VPN access to and/or create custom accounts by clicking on Add someone. When you're done, click on Next.
- Select Through the Internet, and click Next.
- Select the protocols you want to enable for this connection. You'll likely want to select Internet Protocol Version 4 (TCP/IPv4), so remote users receive an IP address and can access the Internet and/or network. Plus if you want the remote user(s) to access file and/or printer shares, select File and Printer Sharing for Microsoft Networks. When you're done, click Allow access.
- On the next window, click Close.
Now you need to access the properties of the newly created incoming network connection and define the IP address range for VPN clients:
- On the Network Connections window, double-click Incoming Connections.
- Select the Networking tab and double-click Internet Protocol Version 4 (TCP/IPv4).
- Select Specify IP addresses and then enter a starting and ending address that's within range of your local subnet but not conflicting with the DHCP range. For example, if your router's IP is 192.168.50.1, you might enter 192.168.50.50 to 192.168.50.59 which would support 10 clients. If you want clients to be able to assign themselves an IP, select that option.
- Click OK on both dialog boxes to save the changes.
Configure any third-party firewalls
Windows will automatically allow the VPN connections through Windows Firewall when you configure the incoming connection on the host PC. However, if you have a third-party firewall installed on the host PC, you need to make sure the VPN traffic is allowed. You may have to manually enter the port numbers 47 and 1723.
Configure your IP address, dynamic DNS, and router
To enable VPN connections to the host PC from the Internet, you must configure your router to forward them to the Windows PC that's accepting the incoming connections. You specify the host PC by entering its local IP address. Therefore, before you setup the port forward, you should ensure the IP address won't change.
Start by logging into to the Web-based control panel of the router. Then go to the Network or DHCP settings and see if you can reserve the IP address for the PC so it always gets the same one. This may be called DHCP reservation or Static DHCP. Some routers don't have this feature. In this case, you'll need to manually assign the PC a static IP in the TCP/IP settings of the network connection in Windows.
Once you have figured out the IP address, find the virtual server or port forwarding settings in the router's web-based control panel. Then create an entry forwarding port 1723 to the local IP address of the PC, such as Figure 6 shows. Don't forget to save the changes!

If your Internet connection uses a dynamic IP address, rather than a static one, you should signup and configure a dynamic DNS service. This is because when you configure the remote clients, you have to input the Internet IP address of where the host PC is located. This will be a problem if the IP changes. However, you can sign up for a free service, such as from No-IP, and input your account details into the router so it will update the hostname with your IP. Then you'll have a hostname (such as yourname.no-ip.org) to input into remote clients, which will always point to the current Internet IP address of your host PC.
Now everything on the server side should be configured and ready to go. Next you need to setup the clients.
Create outgoing VPN connections in Windows
Now that you have the server setup, you need to configure the computers which you want to connect from, called the VPN clients. Here's how to in Windows Vista and 7:
- Right-click the network icon in the system tray and select Open Network and Sharing Center.
- Click Set up a connection or network (Windows Vista) or Set up a new connection or network
- On the wizard, select Connect to a workplace, and click Next.
- Select Use my internet connection (VPN).
- Type the Internet IP address or hostname into the Internet address and enter something for the Destination name. You'll probably want to keep the other options disabled. Click Next to continue.
- Enter a User name and password that was selected when you created the incoming VPN connection, and click Next to try to connect. It will attempt to connect using the following protocols: SSTP, PPTP, and then L2TP.
- Once connected, click Close.
Windows may by default assign the connection as a Public Network, limiting sharing functionality. Therefore you probably want to change this. If you aren't prompted to do so, open the Network and Sharing Center and click Customize (Windows Vista) or the Public network link under the connection name (Windows 7). Then on the popup window, select Work Network.
Here's how to create and outgoing VPN connection in Windows XP:
- Open the Network Connections window and click Create a new connection.
- Select Connect to the network at my workplace, and click Next.
- Select Virtual Private Network connection, and click Next.
- Enter a name for the connection, and click Next.
- Select Do not dial the initial connection, and click Next.
- Type the Internet IP address or hostname, and click Next.
- Click Finish.
Limiting VPN traffic
By default, all the Internet traffic on the VPN client will pass through the VPN rather than the local Internet they are connected to. This is great if they are using a public connection, like a port in a hotel or Wi-Fi hotspot, since it keeps their browsing private. However, if they are on a trusted network, like at their home or remote office, this just might be wasting bandwidth. To limit the traffic that passes through the VPN connection:
- On the Network Connections window, right-click the VPN connection and select Properties.
- Select the Network tab and double-click Internet Protocol (TCP/IP).
- Click the Advanced button and uncheck Use default gateway on remote network.
- Click OK on the dialog boxes to save changes.
Now the VPN client will use the local Internet connection when browsing websites. It will only use the VPN connection when a server or IP address isn't reachable via the Internet, such as when accessing shares on the VPN host network.
Connecting to the VPN
In Windows XP, you can connect and disconnect by opening the Network Connections window and right-clicking the VPN connection. In Windows Vista, you can click the network icon in the system tray, click Connect to, and then select the connection. In Windows 7, click the network icon in the system tray and select the VPN connection.
After you connect, you should be able to access the shared resources on the VPN host network. Keep in mind; you may have to manually access shares (e.g. ip_address_of_computer or file://computer_name/) rather than browsing in My Network Places or Network.
Thursday, September 13, 2012
Kismet
The goal for this post was really just a quick way to get Kismet up and running and then viewing the output quickly.
I will just detail the steps to get this working and what to do with the data once you have collected it. I am using BackTrack 5 r3 within a Virtual Machine and an Alfa AWUS036H set at 30db. You can skip step 2 if you are not using a virtual machine.

Select your interface preference . I chose [ Yes]











I will just detail the steps to get this working and what to do with the data once you have collected it. I am using BackTrack 5 r3 within a Virtual Machine and an Alfa AWUS036H set at 30db. You can skip step 2 if you are not using a virtual machine.
1. UPDATE BACKTRACK!!!
- root@bt:~# apt-get update && apt-get dist-upgrade
- Let this complete, it may take upwards on 2-5 minutes depending on if its a fresh install.
2. Plug in your Alfa, connect it to the VM and restart networking
- Connect the Alfa USB to the VM by performing the steps below. Additionally you can use the icon row at the bottom of VMware workstation to connect the device. With Fusion, simply click Virtual Machine // USB // Connect Realtek [Model]
- Once the adapter is attached to the VM, restart networking… just to have a clean attachment.
- root@bt:~# /etc/init.d/networking stop
- root@bt:~# /etc/init.d/networking start
- Check that the adapter has been detected and is functioning by checking iwconfig
- root@bt:~# iwconfig
- Determine what interface is associated with your Alfa (Realtek RTL8187) chipset.
- root@bt:~# airmon-ng
- In my example we are going to use: wlan0 (zero)
- root@bt:~# iwconfig
3. Update Kismet
- Grab the latest version from http://www.kismetwireless.net/download.shtml and install it. Be sure to review ALL documentation here.
- root@bt:~# wget https://www.kismetwireless.net/code/kismet-2011-03-R2.tar.gz (or whatever the latest version is)
- root@bt:~# tar xvfz kismet-2011-03-R2.tar.gz
- root@bt:~# cd kismet-2011-03-R2
- root@bt:~/kismet-2011-03-R2# ./configure
- root@bt:~/kismet-2011-03-R2# make install (this may take upwards of 5 – 10 minutes)
4. Start Kismet
- Be sure to read the kismet help file for all available switches. I am purposely NOT using -c to specify an interface.
- root@bt:~# kismet
- Note: If you are not going to use GPS, edit your kismet.conf file and tell it you are not going to.
- root@bt:~# vi /usr/local/etc/kismet.conf
- Edit the line: Do we have a GPS? to say “gps=false”
- Helpful navigation tips. [TAB] moves selection. [`] Brings up menu items, arrow and enter keys allow interaction between items.

Select your interface preference . I chose [ Yes]
- After choosing interface options, you will be ‘reminded’ that kismet is running as root. Be sure to determine the risk before answering.

- Choose if you would like to start the kismet server. Kismet runs in a client/server configuration. More details here. Note, once you start the server, a number of files will be generated and placed on your desktop. (Assuming you started kismet within that directory) Do not delete these files, they are the logs of the captures.

- Select [ YES ] to add an interface for raw capture.

- Enter the interface you are going to use (from step 2) and enter any options or name and select [ Add ]

- An error about dhclient looking at the adapter you have chosen will appear if you have not stopped the service. To stop it specifically for your wireless adapter, just look at the open files and kill the dhclient service attached to wlan0.
- root@bt:~# lsof | grep wlan0
- root@bt:~# kill -9 [PSID]

- To view the traffic Kismet is seeing, you will need to close the console. (Don’t worry, you can get it back if you need)

- The Kismet menu system can be engaged by pressing the [`]or [~] and then use the arrow keys to navigate.

- To interact with the visible networks, head over to the sort menu and select your sorting preference. I chose [ type ] for this example. You can select the network you want more details about by navigating to it and pressing enter.


5. Reviewing Captures
Now Kismet has been capturing data, how can we look at it?- You should have 5 files (depending on your switches and options you may end up with more or less.
-
- Kismet-[ date/time].netxml
- Kismet-[date/time].gpsxml
- Kismet-[date/time].alert
- Kismet-[date/time].nettxt
- Kismet-[date/time].pcapdump
- To view the .netxml file in excel, simply rename and drop the [net].

- Then simply import the .xml file into excel.
- In excel 2010, I was only able to open the data in read only mode.

- To view uptime in days, for the AP’s. Josh Wright has provided a nice formula we can use.
- Apply: =U[cell]/(1000000 * (60 * 60 * 24)) to the “/bsstimestamp column.
- Example: =U70/(1000000*(60*60*24))
- Row 76 becomes 77, where row 77 contains the time in Days in the last column.
Wrap up
There are many ways to view and capture data with Kismet, using xplico plus the .pcap could prove useful. I have only scratched the surface of what is possible. The purpose of this post wasn’t to include every possible combination, but to get you up and running quickly using kismet and reviewing the data just as fast.
Subscribe to:
Posts (Atom)